Intrusion detection attacks Intrusion detection system -the intrusive behavior of security Intrusion detection system
How Works Intrusion Detection System - Assignment Point
Detection intrusion Intrusion detection ppt ids system glance slideshare Intrusion detection
Intrusion ids ips jaringan serangan pendeteksi penahan access intruders pengertian tkj
Intrusion detection system pptWhat is intrusion detection system [ids]? Detection intrusion systemDetection intrusion system ppt slideshare.
Intrusion systems componentsIntrusion detection system. The intrusion detection system and external/internal network intrusionIntrusion detection ids system types systems protection modes operation benefits candid technology tech.

Schema of the proposed intrusion detection system
Intrusion detection system architecture response algorithms figure directions fundamentals requirements futureIntrusion detection system(ids) at a glance (ppt) Top 10 best intrusion detection systems (ids) [2023 rankings]Intrusion detection systems & solutions.
Intrusion security intrusiveIntrusion detection system Intrusion softwareIntrusion security rankings threats softwaretestinghelp.

What is an intrusion detection system and how it helps?
Intrusion detection academiaIntrusion detection system: benefits, types and modes of operation What is intrusion detection system? in easy way(pdf) intrusion detection system.
Intrusion detection system works management business assignment point assignmentpointOverview of intrusion detection system Intrusion detection systemHow works intrusion detection system.
![What is Intrusion Detection System [IDS]? - UseMyNotes](https://i2.wp.com/usemynotes.com/wp-content/uploads/2021/02/what-is-intrusion-detection-system.jpg)

How Works Intrusion Detection System - Assignment Point
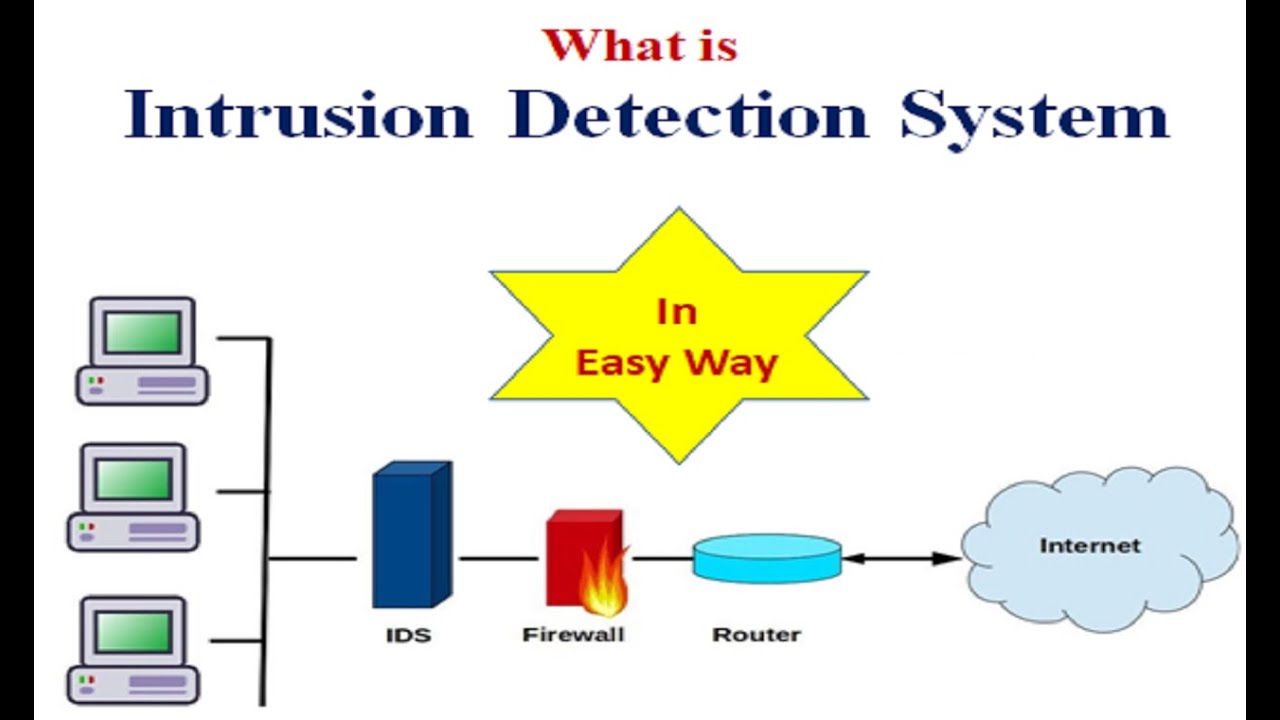
What is Intrusion Detection System? In Easy Way - YouTube

Intrusion detection system | TechnoWhiz

(PDF) Intrusion Detection System | Dr. Rajendra Maurya - Academia.edu

Intrusion Detection System - Krazytech

Schema of the proposed Intrusion Detection System | Download Scientific
![Top 10 BEST Intrusion Detection Systems (IDS) [2023 Rankings]](https://i2.wp.com/www.softwaretestinghelp.com/wp-content/qa/uploads/2019/12/Intrusion-Detection-Systems.png)
Top 10 BEST Intrusion Detection Systems (IDS) [2023 Rankings]

What Is an Intrusion Detection System and How It Helps? - TECH PRO DATA

Algorithms | Free Full-Text | From Intrusion Detection to an Intrusion